An onion site recently sprung up, which was mentioned by a few pepoleover the last few days, for claiming to have hacked BitFinex. This site is a copycat of a hacking group from a few years ago and many people (including myself) assumed it was the same group.
Earlier today I made a poorly worded X post (“BitFinex breach confirmed”), which ultimately got editorialized and resyndicated across many “Headline accounts”. I’m not sure if these were human or AI, but it ended poorly.
The Error
The fundamental error in my thinking was, that upon confirming the username and passwords worked as intended (prompting a 2fa). I wanted to get a post out quickly for the sake of encouraging people to change their usernames and passwords, I also tagged Paolo, which led to a statement that ultimately killed this rumor.
Per Paolo, only 5k of the 22k accounts are BitFinex accounts. I tested a few near the top (the first and a few down), which were likely curated by this group to create the illusion of legitimacy.
What actually likely happened here, is that the passwords were obtained from other breaches, all of the working accounts I found, were also in the CoinMarketCap breach. Every email (including ones that did not login) has multiple haveibeenpwned entries, mainly on less sensitive sites which may not have taken as much precaution.
Paolo also noticed that many of these accounts also worked on other crypto CEXes. Password reuse is a major no for any accounts, especially those with financial privileges.
Original Article:
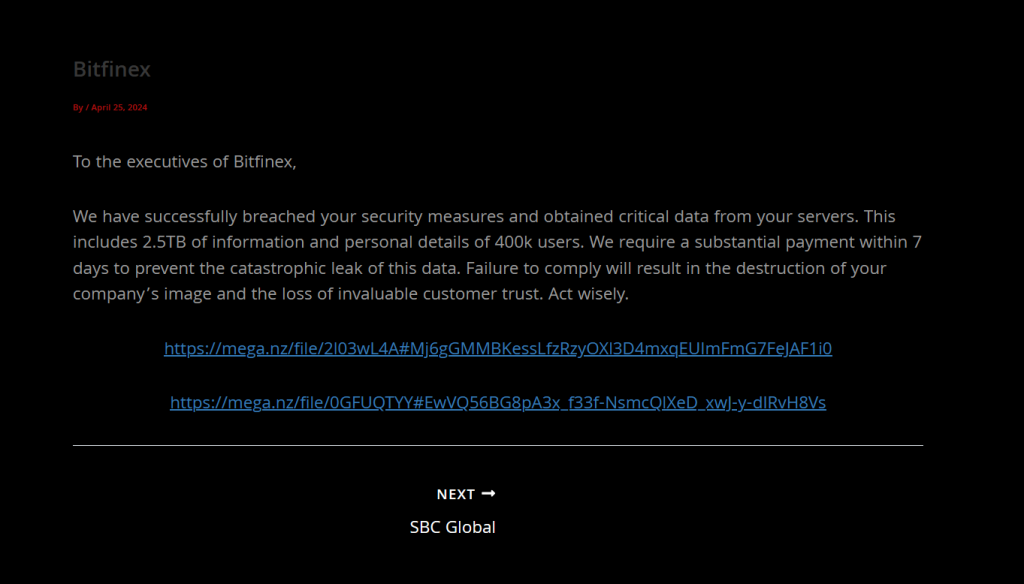
The FSociety ransomware group have uploaded this page on their onion site, along with 2 mega links which lead to a txt file containing a partial dump of usernames and plaintext passwords. From searching, my own bitfinex account is not in this list, nor are any of the ones known to belong to trading firms (IE alameda research).
They claim if their demands are not met, they will also leak KYC for all users. Given the huge quantity, it would appear they have access to every KYC document since inception.
The following is a list of email domains from this leak. The only ones of potential interest is coinfarm.co.za. Pretty much all of these are public email domains, not corporate ones, it’s possible the hacker intentionally trimmed those accounts.
ymail.com,yahoo.com,outlook.com,gmail.com,yahoo.co.uk,me.com,hotmail.com,ya.ru,163.com,mail.ua,rogers.com,gmx.de,gardener.com,yahoo.ca,vt.edu,t-online.de,live.com,web.de,naver.com,googlemail.com,ukr.net,posteo.de,mail.ru,yandex.ru,verizon.net,aol.de,rambler.ru,bk.ru,hotmail.de,126.com,crobads.com,my.fsu.edu,aol.com,hotmail.no,msn.com,angiang.edu.vn,yahoo.fr,shaw.ca,icloud.com,att.net,yahoo.com.br,o2.pl,spedition-kern.com,nate.com,gmx.at,freenet.de,yandex.com,yahoo.it,yopmail.com,daum.net,vaseo.co.za,semenov.ru.com,mail.com,lantic.net,protonmail.com,hotmail.ca,yahoo.es,live.de,uol.com.br,live.nl,ua.fm,sdtransportllc.com,live.se,hotmail.co.uk,comcast.net,mac.com,inbox.ru,qq.com,aim.com,bigmir.net,yahoo.in,abv.bg,yahoo.com.tw,seznam.cz,rocketmail.com,dbit.co.za,hotmail.it,hotmail.fr,yahoo.co.in,live.it,yahoo.co.kr,bigpond.com.au,live.co.uk,g8k.com,codycagle.com,vpstraffic.com,my.com,nektardata.com,cafedecolombia.com.co,leokey.com,yahoo.ro,polskidruk.com.pl,411development.com,maxpromonepal.com.np,alice.it,gmx.net,bigpond.com,genuineromanart.com,gus.pittstate.edu,gci.net,hotmail.co.za,izver.com,example.com,live.com.mx,mavrsoft.com,mediabattles.com,coinfarm.co.za,rediffmail.com,familyone.org,sbcglobal.net,libero.it,sorservicesinc.com,yahoo.de,microitlabs.com,e-mail.com.tr,ringcentral.com,sky.com,hotmail.com.br,yahoo.com.hk,warah.com.ar,hanmail.net,wp.pl,interia.pl,uncc.edu,extrageld.online,onet.pl,outlook.de,krebber-online.de,btcexpert.com,arcor.de,lightmaregaming.net,infranetwireless.net,cox.net,ecord.us,sympatico.ca,obtrix.net,plexus.co.za,myrambler.ru,usa.com,parkingaccess.com,iamjohnwhite.com,hidlostudios.com,wskandsons.com,pullicino.de,live.fr,luxmail.com,ccdcweb.com,bellsouth.net,azet.sk,justice.com,zoho.com,list.ru,outlook.fr,bol.com.br,unida.ac.id,windowslive.com,icos.best,outlook.it,charter.net,admins.lt,szonevn.com,aiesec.net,imoos.com,yahoo.co.jp,ccamm.com,clemzcorp.com.ng,darkman.info,inbox.lv,yandex.ua,interia.eu,telenet.be,actionmarketingplus.com,hotmail.es,yahoo.co.id,yahoo.com.ph,hotmail.co.th,outlook.es,mail.bg,hotmail.cl,villa-community.com,hotmail.se,hotmail.com.au,my.bristol.ac.uk,bns-uk.com,queensu.ca,herbinartisans.com,gmx.com,gmx.us,furre.biz,maildrop.cc,hushmail.com,secmail.pro,hotmail.gr,hughes.net,hostcalls.com,cyber-rights.net,orange.fr,ruggedinbox.com,mailinator.com,fastmail.se,mail2tor.com,europe.com,op.pl,monkeybaittackle.com,nrmchospital.org,stlprioryschool.org,greenfuelh2o.com,uniandes.edu.co,nu.edu.kz,vols.utk.edu,eckerd.edu,live.ca,familiapraca.com,muslim.com,live.be,gmx.fr,vail.net,creighton.edu,andreaskurniawan.web.id,tpg.com.au,yahoo.com.ar,ucs.org.uk,live.ru,i.ua,digitalshift.co.uk,stevengeorgeharris.com,bizhat.com,jaspin.com,live.dk,yahoo.no,live.com.au,live.com.pt,cccb.edu,utoronto.ca,hotmail.lt,upr.edu,msu.edu,alumni.lsu.edu,yahoo.gr,outlook.com.br,lucasforesti.com.br,hotmail.com.ar,email.cz,slusd.us,mfac.edu.au,siggifly.net,caulfieldgs.vic.edu.au,home.nl,gamil.com,tim.it,gmail.co,centrum.cz,netmails.info,mweb.co.za,kpnmail.nl,gmail.comi,centrum.sk,shanefarnsworth.biz,yahoo.pl,ahzo.nl,upcmail.nl,srbrail.rs,gmali.com,hetnet.nl,mailprotech.com,sapo.pt,zeelandnet.nl,btinternet.com,iba-group.com,tourplayermarketing.com,thismail.ru,zwoho.com,gmx.ch,huayyangliving.com,dr.com,gmaile.com,sbb.rs,blogtout.fr,gmai.com,online.de,hotmail.nl,tiscali.it,yahoo.ie,comfsm.fm,meta.ua,hotmail.be,gmail.com.vn,yahoo.com.vn,poczta.fm,zoznam.sk,ytahoo.com,ieselcalamot.com,post.cz,t-mobilethuis.nl,hotmail.rs,new-online.de,gmail.hu,indiansun.com.au,ziggo.nl,alexishallconsulting.com,citromail.hu,gmail.comeb,zonnet.nl,idolme.net,st.ueh.edu.vn,iafrica.com,presbyuniversity.edu.gh,bee-rollproduction.com,sccoast.net,singnet.com.sg,bellsouth.com,mail.ccsf.edu,rolmail.net,hallo.ms,email.com,artofhealthyfreedom.com,moerk.nl,outlook.be,investissezenvous.biz,spoko.pl,nando1.com,classic-hohenhameln.de,top.it,virgilio.it,hotmailpro.info,expectancy.co.uk,providier.com,outlook.ph,fpt.edu.vn,email.it,irmbor.co.rs,gmail.con,gemail.com,walla.com,earthlink.net,pki.nl,tlen.pl,yopmai.com,54u54me.com,planet.nl,roxbury.edu,mjandersen.com,gmx.biz,consultant.com,tutanota.com,frontier.com,bld.vn,ignaciaheyer.com,mcleister.com,webmail.co.za,zorghanden.nl,yellville.net,gimai.com,lebarongroup.com,buscacio.net,222gmail.com,live.in,inwind.it,autograf.pl,sulive.com,passiveincomeswithscott.com,gmaill.com,outlook.co.th,sirius.hr,inpolnetwork.cz,5x2.de,gamail.com,send22u.info,mpww-lebenstraeume.de,gmil.com,mail.dk,vanixa.com,messing-goertz.de,sitedesignhelp.com,wp.eu,stu.clcillinois.edu,cable.net.co,teletu.it,systemlauncher.com,sccomunicazione.net,talktalk.net,naturain2011.it,mandarinasoft.cat,bidv.com.vn,gnail.con,bluewin.ch,btopenworld.com,null.net,jubii.dk,boo.pl,ezvib.com,digital-filestore.de,email.de,royalestateproperties.com,media-vision.be,yahoo.com.au,werbestudio-koeln.de,freemail.hu,telfort.nl,tin.it,outlook.sa,gail.com,mailzapper.de,gmaill.co,isisbem.it,zhedel.com,fix.com.do,wharton.upenn.edu,virginia.edu,aclass.az,caucasus.net,nextsource.com,notes.udayton.edu,cantv.net,fastwebnet.it,cwh.org.uk,myself.com,skillvillegames.com,smart60.ru,suddenlink.net,tds.net,myspace.com,gwmail.gwu.edu,ruutli.com,sandiego.edu,generali.ie,prodigy.net.mx,umbee.couk,mwdata.net,comcast.ney,clientfirstmortgages.com,mykapoor.com,thallium.nl,duck2.club,laposte.net,fbi.al,tut.by,free.fr,gulli.com,rediff.com,modcom.net,fcorsec.com,fabianofernandes.adm.br,hoangdao.com,mynet.com,maesys.net,kiraly.sk,yahoo.com.tr,hotmai.com,yandex.by
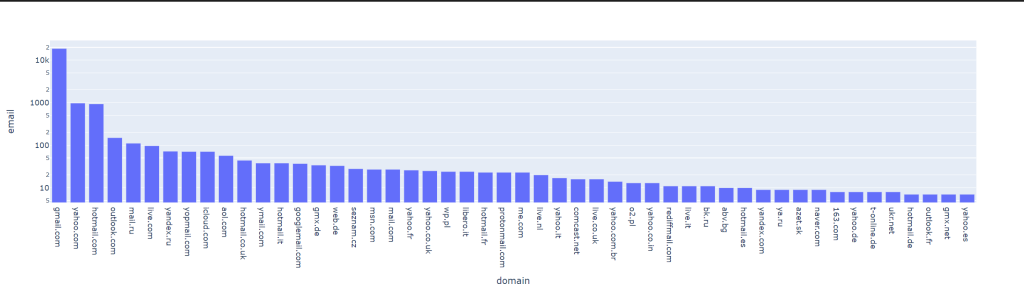
Alternatively we can plot the frequency of emails. Gmail is far and away the winner, and beyond that, things get much smaller (log scale).
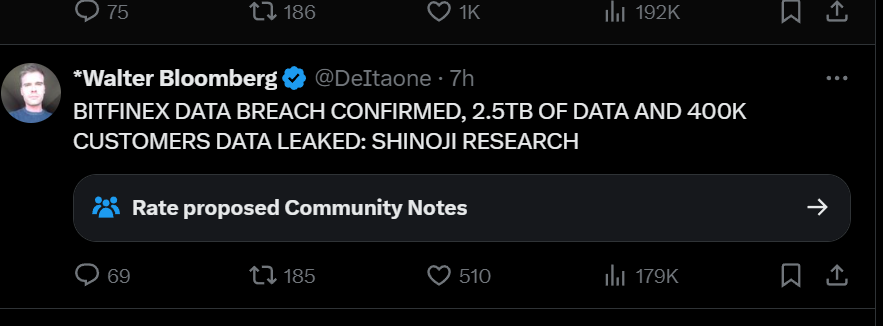
UPDATE Breach Confirmed.
A follower of mine happened to try one of the passwords in the file by chance, and got a 2fa prompt. I tested it just now and I can confirm, the breach is not fake.
I have tagged Paolo, and will see if anyone else may be a relevant contact. I hope the second part of the claim is not true.
Update 2: Paolo Response
Paolo Ardonio responded, suspecting this data originated from another breach, and not BitFinex. He additionally claims that the hackers never reached out to BitFinex.
Given no bitcoin address is posted on the site, it would appear they would have no way of paying the ransom (without private communication). Given that you have to question the motivation of the “Fsociety group”.
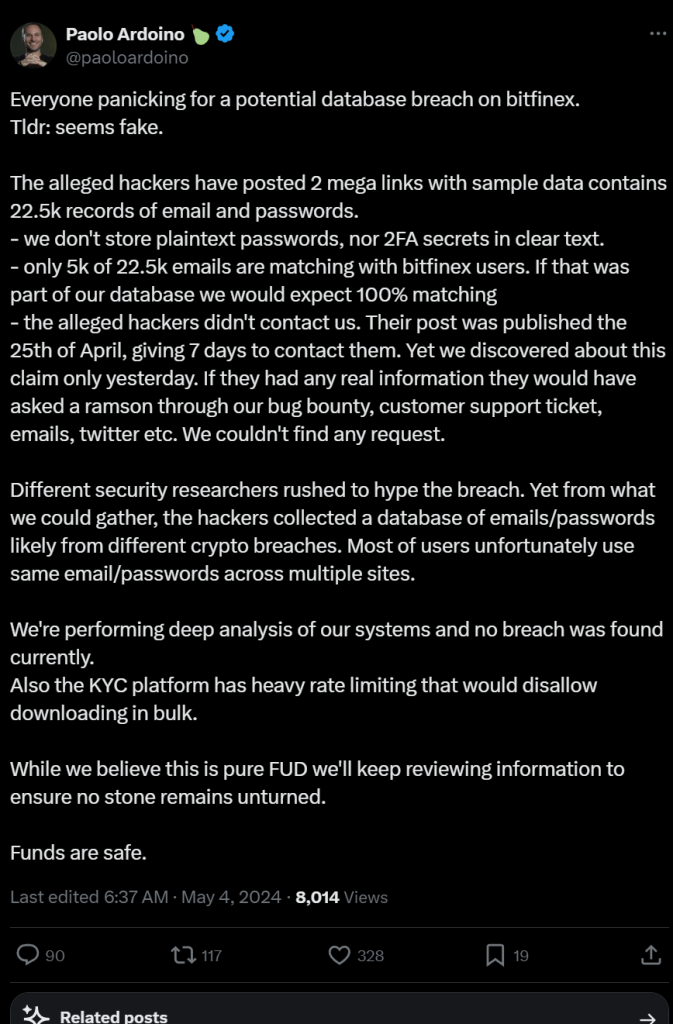
Paolo also points out the KYC system has heavy rate limiting, and they do not store passwords in plaintext. So where did the passwords come from?
Assuming he is telling the truth, all of these accounts have heavy presence on HaveIBeenPwned. Many of the logins are from the Coinmarketcap breach.
Some of the accounts don’t come from that one. It is possible that the list was constructed in reverse (by taking breached passwords and trying them on BitFinex), but it’s not obvious why.
The list is not being sold, it’s available for free download from the hackers site. They did not actually extort bitfinex, so then what is the scheme. Were they planning on charging for a fake KYC database?
It seems the answer has been found. F Locker is trying to advertise some seedy investment in their ‘breaches’.
Leave a Reply